The network at Loeppenthien.NET
Network Site Protection Cisco IOS Commands
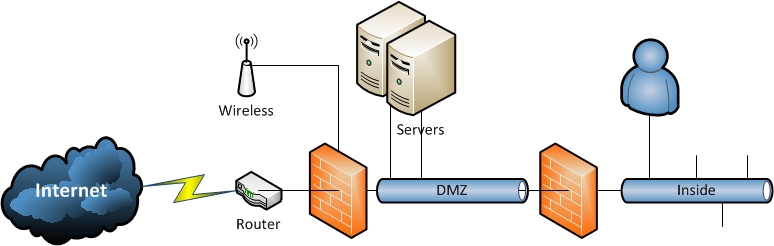
Below is a simplified network drawing of the network at Loeppenthien.DK
When I started to build my network my knowledge of Cisco IOS were limited. This is why I have build a page with some of the commands that I have used from time to time - Cisco IOS Commands.
Router
A router is in general a device that translate traffic between 2 different subnet or network types. I my case it translate from a public IP-address to my private network.
This router handles all the internet traffic. In order to minimize the workload of the firewall behind, external access on some ports have been blocked.
access-list 100 deny icmp any any redirect
access-list 100 deny udp any any eq 19
access-list 100 deny tcp any any eq 31 syn
access-list 100 deny tcp any any eq 41 syn
access-list 100 deny tcp any any eq 58 syn
access-list 100 deny tcp any any eq 90 syn
access-list 100 deny tcp any any eq 121 syn
access-list 100 deny udp any any eq 135
access-list 100 deny tcp any any eq 135 syn
access-list 100 deny udp any any range 136 140
access-list 100 deny tcp any any range 136 140 syn
access-list 100 deny tcp any any eq 421 syn
access-list 100 deny tcp any any eq 456 syn
access-list 100 deny tcp any any eq 531 syn
access-list 100 deny tcp any any eq 555 syn
access-list 100 deny tcp any any eq 911 syn
access-list 100 deny tcp any any eq 999 syn
access-list 100 deny udp any any eq 1349
access-list 100 deny udp any any eq 6838
access-list 100 deny udp any any eq 8787
access-list 100 deny udp any any eq 8879
access-list 100 deny udp any any eq 9325
access-list 100 deny tcp any any eq 12345 syn
access-list 100 deny udp any any eq 31335
access-list 100 deny udp any any eq 31337
access-list 100 deny udp any any eq 31338
access-list 100 deny udp any any eq 54320
access-list 100 deny udp any any eq 54321
For a better understanding of the individual port numbers see this page - Port Numbers
Firewall
In general a firewall is a gatekeeper. This device decides what traffic is allowed and what should be blocked. The rules can be designed by IP-address or port number or both.
By default a firewall allows all traffic from inside to the outside. It blocks everything from the outside (Internet) to the inside. In order for a web server to work behind a firewall access on port 80 has to be opened. In the link above port numbers for different standard services can be found.
Wireless access point
Wireless access points are today one of the larger security risk in private network. By default they allow access to everybody. ( At the moment I have access to 3 other access points in the same building, because they haven't been configured.) All access points have the possibility to deny access for everybody except a specific MAC address. This is a very easy way of making sure that it is your computer and only your computer, that is using the access point.
Encryption is another way of securing the access point. Here you give an encryption key to the access point and only netcard with the same encryption key is able to connect.
It is very hard to prove that someone have misused your internet line, by accessing your wireless access point.
So protect your self and your network ![]()
Monitoring the Network
In order to monitor the network traffic on Loeppenthien.dk and Loeppenthien.NET, a MRTG service was been installed on the web server. This service gives some information of the traffic and status of the routers. It is not an alert tool, which can take any action in case of a line failure. The advantage of MRTG is it huge options for customization.
MRTG however could not for fill our need in the long run, so we switch to use Paessler PRTG. PRTG comes with an intuitive setup function, and is able to detect and configure monitoring for both network equipment and servers. PRTG is available in a free version, with 10 probes. This is normally enough for private persons. For more information click the logo below:
